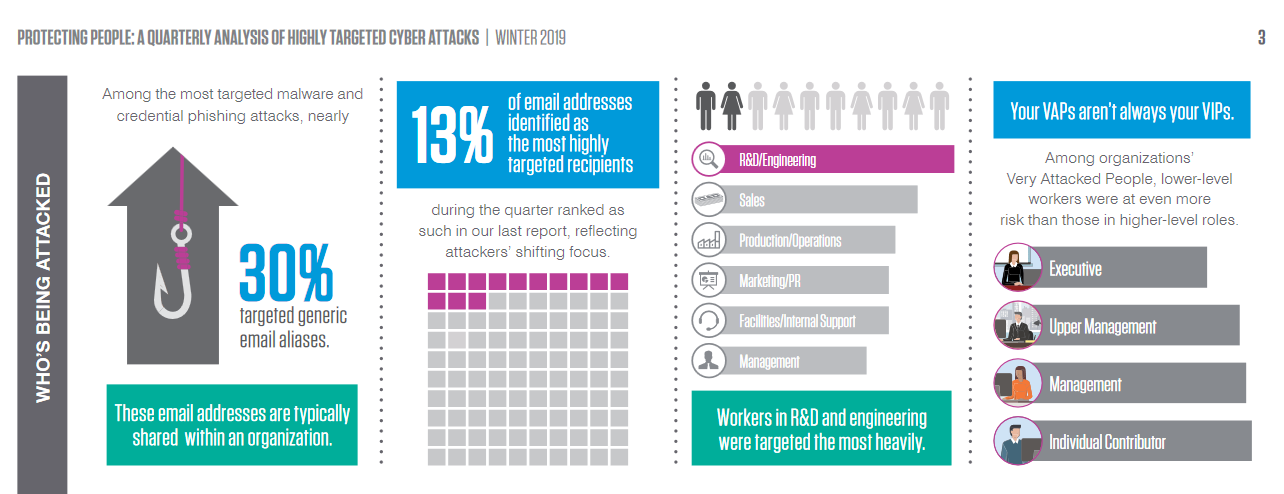
Targeted Attack Protection
Protect against advanced threats with the industrial the most robust email security platform and the most accurate view of the email threat landscape.
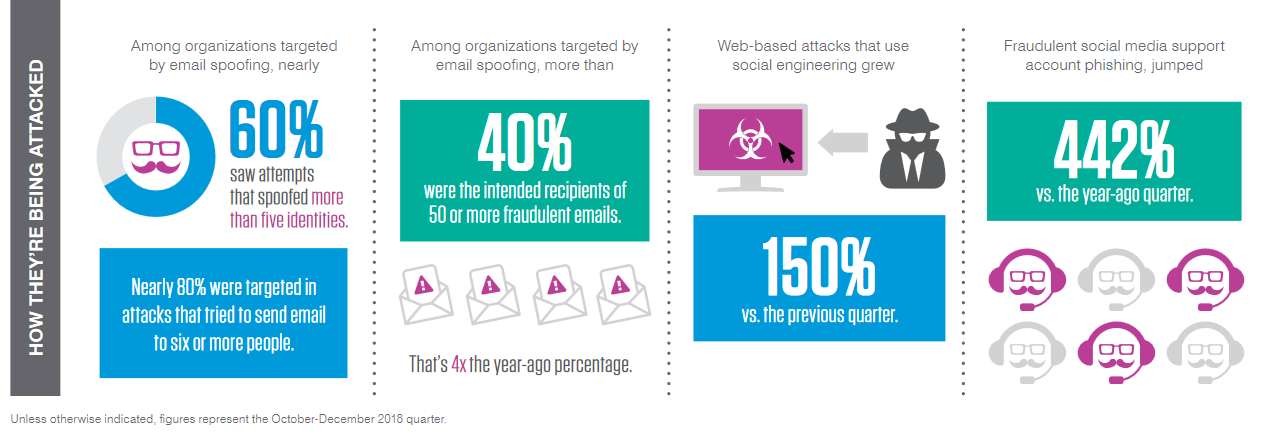
Threat Response
Respond faster to incidents by automating and streamlining manual tasks. Manage incidents across your entire security infrastructure in a single view.
ET Intelligence
Apply fully verified threat intelligence that includes proof of conviction, data on more than 40 threat categories, five-year history, and related samples, domains, and IPs.
Ransomware is a big ISSUE
Ransomware is a type of malicious software that blocks access to a computer system or data, usually by encrypting it, until the victim pays a fee to the attacker. In many cases, the ransom demand comes with a deadline. If the victim doesn't pay in time, the data is gone forever.
Ransomware attacks are all too common these days. Major companies in North America and Europe alike have fallen victim to it. Cyber-criminals will attack any consumer or any business and victims come from all industries.
Several government agencies, including the FBI, advise against paying the ransom to keep from encouraging the ransomware cycle, as does the No More Ransom Project. Furthermore, half of the victims who pay the ransom are likely to suffer from repeat attacks.
Examples of Ransomware
By learning about the major ransomware attacks below, organizations will gain a solid foundation of the tactics, exploits, and characteristics of most ransomware attacks. While there continues to be variations in the code, targets, and functions of ransomware, the innovation in ransomware attacks are typically incremental.
- WannaCry powerful Microsoft exploit was leveraged to create a worldwide ransomware worm that infected over 250,000 systems before a killswitch was tripped to stop its spread. Proofpoint was involved in finding the sample used to find the killswitch and in deconstructing the ransomware. Learn more about Proofpoint involvement in stopping WannaCry.
- CryptoLocker This was one of the first of the current generation of ransomware that required cryptocurrency for payment (Bitcoin) and encrypted a users hard drive and attached network drives. Cryptolocker was spread via an email with attachment that claimed to be FedEx and UPS tracking notifications. A decryption tool was released for this in 2014. But various reports suggest that upwards of $27 million was extorted by CryptoLocker.
- NotPetya Considered one of the most damaging ransomware attacks, NotPetya leveraged tactics from its namesake, Petya, such as infecting and encrypting the master boot record of a Microsoft Windows-based system. NotPetya leveraged the same vulnerability from WannaCry to spread rapidly, demanding payment in bitcoin to undo the changes. It has been classified by some as a wiper, since NotPetya cannot undo its changes to the master boot record and renders the target system unrecoverable.
-
Bad Rabbit Considered a cousin of NotPetya and using similar code and exploits to spread, Bad Rabbit was a visible ransomware that appeared to target Russia and Ukraine, mostly impacting media companies there. Unlike NotPetya, Bad Rabbit did allow for decryption if the ransom was paid. The majority of cases indicate that it was spread via a fake Flash player update that can impact users via a drive by attack.
Free Ransomware Survival Guide